People Intelligence
The internet is awash with misinformation. iThreat brings clarity.
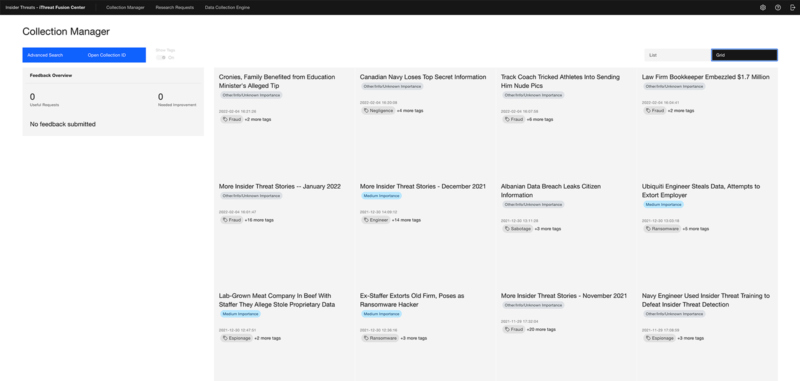
Effective threat discovery helps you plan for and protect against potential unsafe interactions with adversaries, outside or inside your organization. Our platform monitors internet posted dialogue and text to report highly specific intelligence that can help you identify threats to your key personnel.
We cut through signal noise to focus on, analyze, and report only credible intelligence so you can better protect your executives, spokespersons, and your employees.
iThreat Benefits
Flexibility
Investigative Support
Internal Analysis
Executive Research
Embargo Violators
Transparent Platform




Brand managers rely on SignalAlert™ IP Lifecycle Protection to monitor for threats and other sensitive information over the product or service lifecycle, from conception to public availability. We monitor internet dialogue to capture signal intelligence that is relevant to our clients’ brands and are an indispensable partner in identifying IP theft, content leaks, supply chain disruptions, online scams, piracy and more.
Learn MoreSuccessful products are subject to counterfeits and unauthorized uses. iThreat signal intelligence allows you to identify, defend, and respond against counterfeiters, thieves, and adversaries. The iThreat platform also mines relevant data points to drive your analytics to new levels of consumer understanding. Our powerful rules engine and analytical expertise monitors the open, dark, and deep web for relevant signals that can be harmful to your product and brand.
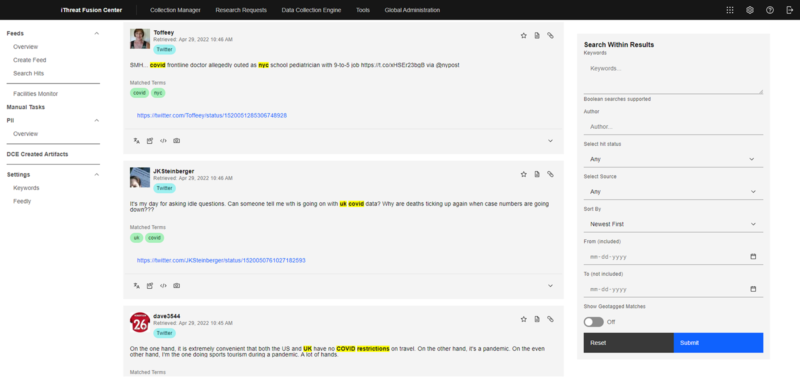
Learn MoreOur platform monitors internet dialogue for critical signals across many data sources to help protect your personnel. From uncovering physical threats directed at key staff to closed group threats targeting business disruptions, iThreat verifies the signal to free your internal security team for action, mitigation and investigation. Manage insider information leaks, unmask embargo violators, and monitor social media activities that can damage credibility and reputation.
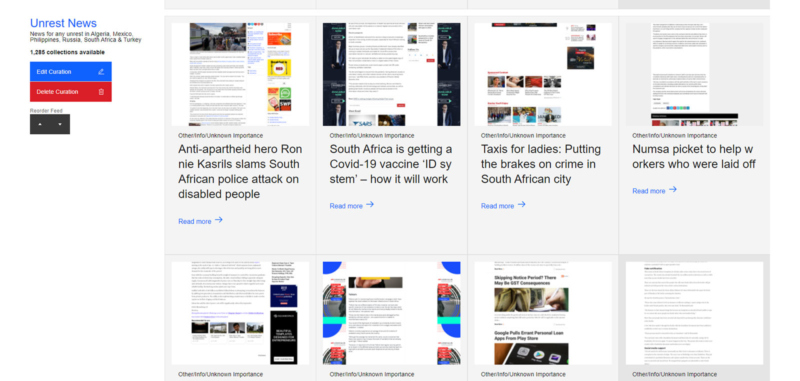
Learn MoreLocalized, closed-source protests, civil unrest, natural disasters, supply chain breakdowns, and global conflicts can disrupt your business and weaken shareholder value. The iThreat platform monitors internet dialogue for critical signals that can predict a risk to your production facilities, information technology, and general business security. iThreat’s platform delivers threat awareness quickly and effectively, enabling your internal security teams to focus on analysis and investigations.
Learn MoreI’m looking to improve:




I’m looking to improve:
Brand managers rely on SignalAlert™ IP Lifecycle Protection to monitor for threats and other sensitive information over the product or service lifecycle, from conception to public availability. We monitor internet dialogue to capture signal intelligence that is relevant to our clients’ brands and are an indispensable partner in identifying IP theft, content leaks, supply chain disruptions, online scams, piracy and more.
Learn MoreSuccessful products are subject to counterfeits and unauthorized uses. iThreat signal intelligence allows you to identify, defend, and respond against counterfeiters, thieves, and adversaries. The iThreat platform also mines relevant data points to drive your analytics to new levels of consumer understanding. Our powerful rules engine and analytical expertise monitors the open, dark, and deep web for relevant signals that can be harmful to your product and brand.
Learn MoreOur platform monitors internet dialogue for critical signals across many data sources to help protect your personnel. From uncovering physical threats directed at key staff to closed group threats targeting business disruptions, iThreat verifies the signal to free your internal security team for action, mitigation and investigation. Manage insider information leaks, unmask embargo violators, and monitor social media activities that can damage credibility and reputation.
Learn MoreLocalized, closed-source protests, civil unrest, natural disasters, supply chain breakdowns, and global conflicts can disrupt your business and weaken shareholder value. The iThreat platform monitors internet dialogue for critical signals that can predict a risk to your production facilities, information technology, and general business security. iThreat’s platform delivers threat awareness quickly and effectively, enabling your internal security teams to focus on analysis and investigations.
Learn MoreFAQ Headline
Our Partners